Overview: Microsoft 365 Apps
Many organizations seek to prevent scripted or unauthorized programmatic access to Microsoft 365 Adversary-in-the-Middle (AiTM) attacks are on the rise, allowing attackers to intercept and forward authentication traffic in real time—even circumventing multi-factor authentication (MFA). A significant development is the adoption of automated user agents such as axios, a JavaScript-based HTTP client, which attackers use to replicate browser activity and take over user sessions.
With these tools, attackers can:
- Automate the collection of credentials and replay of sessions
- Bypass basic browser fingerprinting techniques
- Launch large-scale attacks with minimal manual effort
Although detection strategies like monitoring user-agent strings or identifying unusual geolocation patterns are available, there is a lack of comprehensive guidance on countering these specific threats. Conventional security measures often fail to detect axios-driven requests that closely resemble genuine user actions.
As a result, organizations are exposed to risks including:
- Session hijacking, even when MFA is enabled
- Challenges in distinguishing automated agents from real users
- Ongoing unauthorized access after initial authentication
This blog underscores the urgent need for advanced, behavior-based security measures and enhanced session protection to address these rapidly evolving threats.
Prerequisites
| Requirement | Description |
| Microsoft 365 E5 License | Required for Conditional Access App Control and MDCA session control |
| Microsoft Defender for Cloud Apps | Must be enabled |
| Admin Permissions | You must be an Admin or Security Admin in Entra ID (Azure AD) |
| Pilot Group | Recommended to test with a small group before full deployment |
Step-by-Step Configuration
Enable Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps (MDCA) is a security tool that provides visibility and control over user sessions in SaaS applications. It acts as a reverse proxy when Conditional Access routes a user’s traffic through it
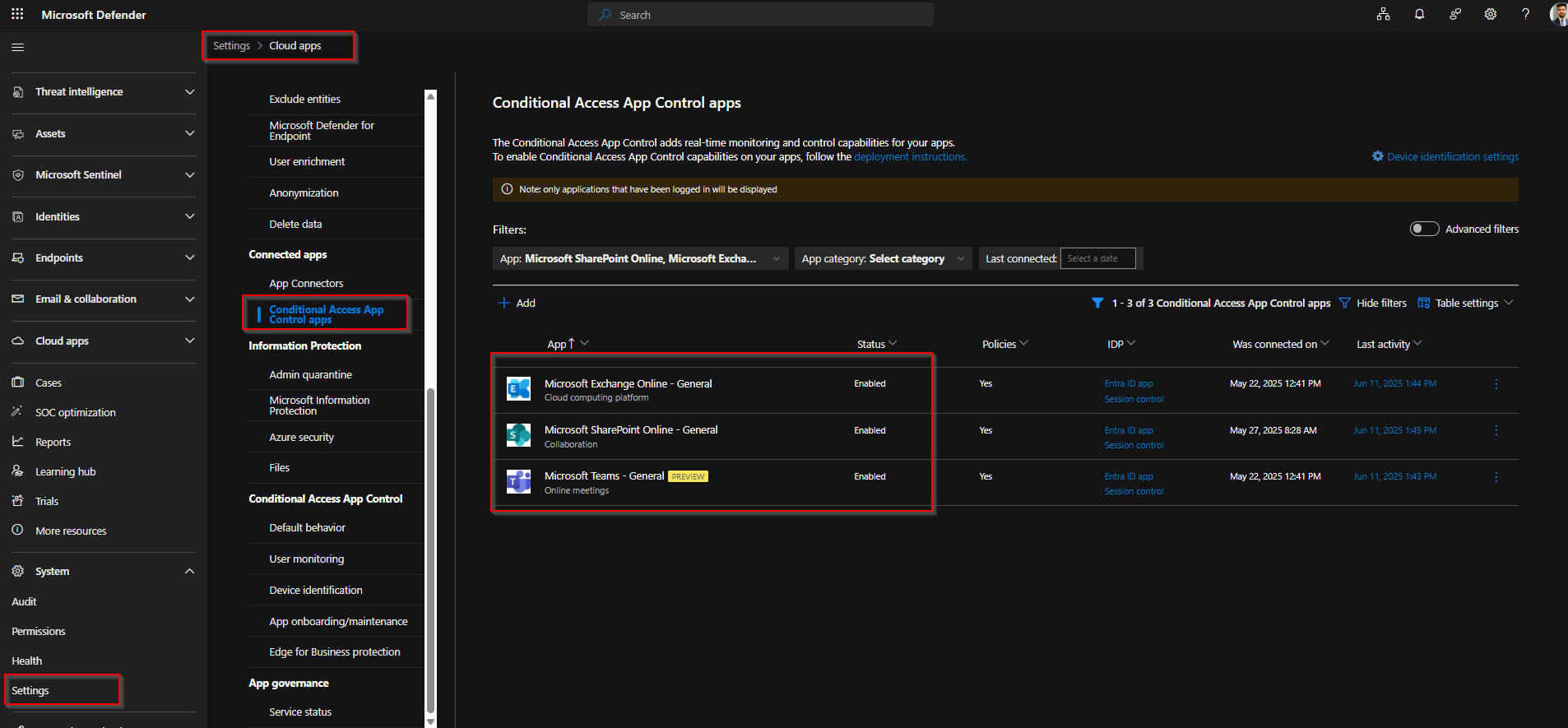
- Go to Microsoft 365 Defender Portal
- Navigate to:
Settings → Microsoft Defender for Cloud Apps → Connected Apps → Conditional Access App Control apps - Ensure Microsoft 365 apps are listed as below. If not, follow below 3.2 steps, to proceed to create conditional access policy for routing the requests to Cloud Apps
Create Conditional Access for Route Traffic to MDCA
Conditional Access App Control sends the session through the MDCA proxy where session inspection happens. This is the foundation for blocking based on the User-Agent string.
Go to Azure Portal → Microsoft Entra ID → Conditional Access
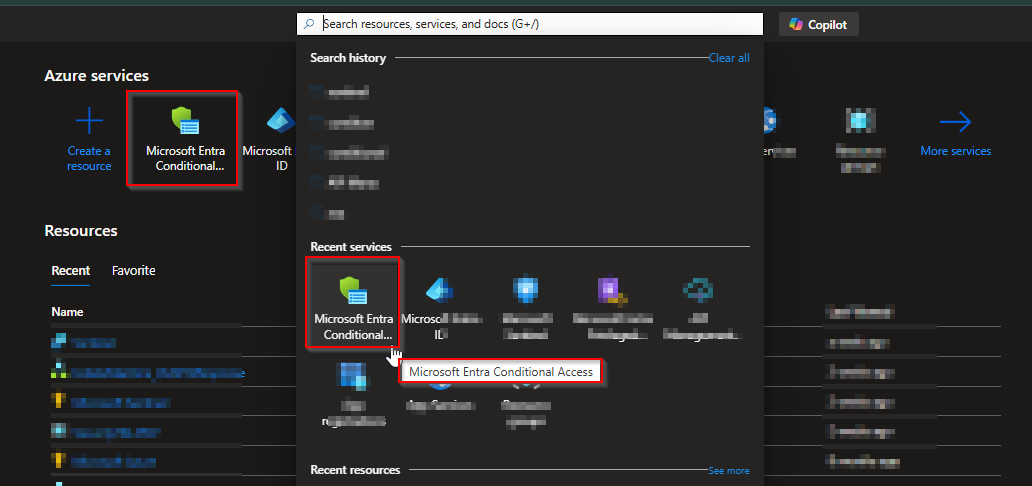
Click + New Policy
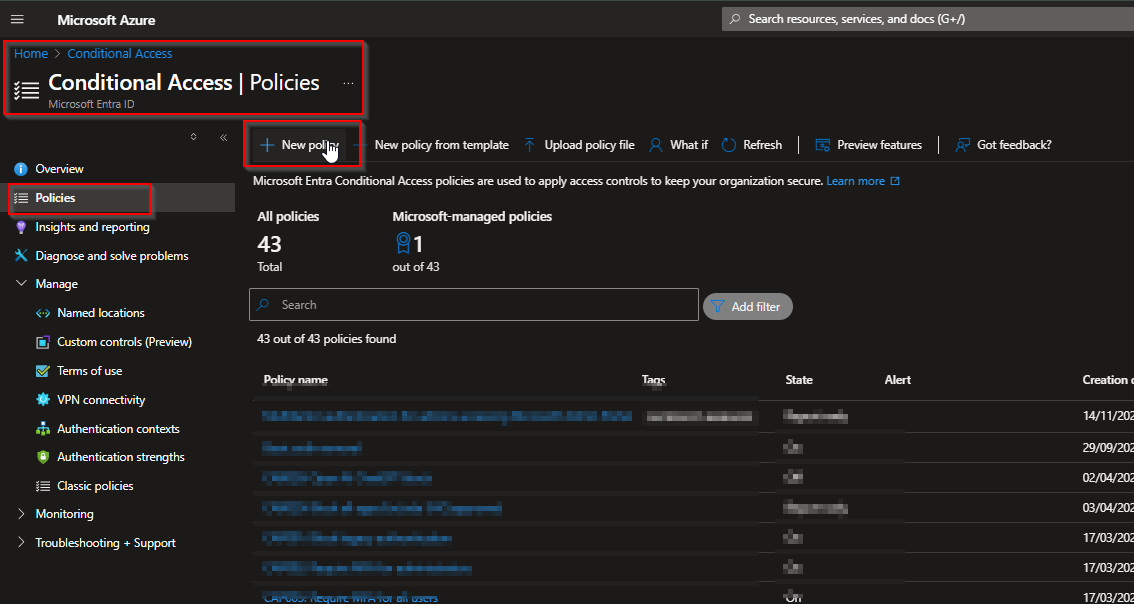
Configure the following settings:
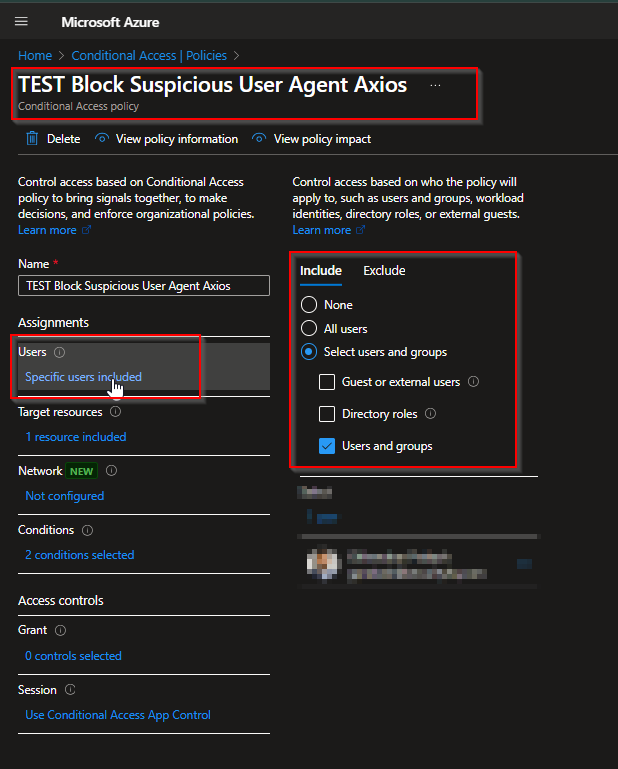
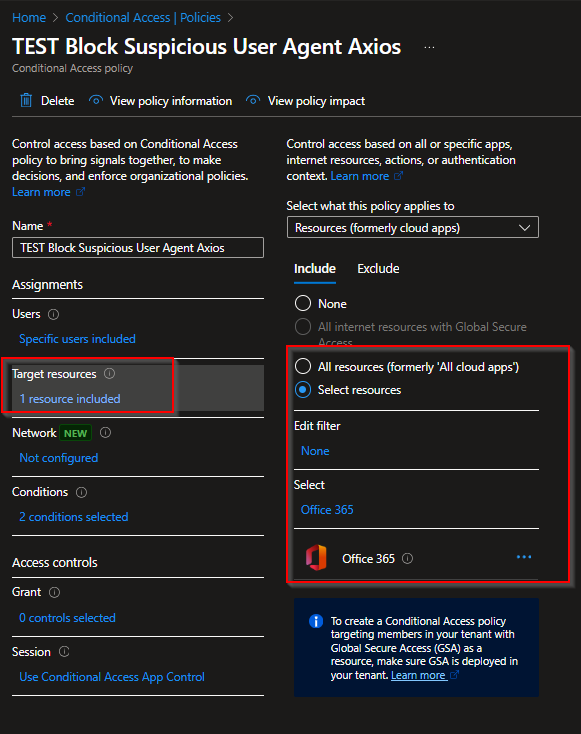
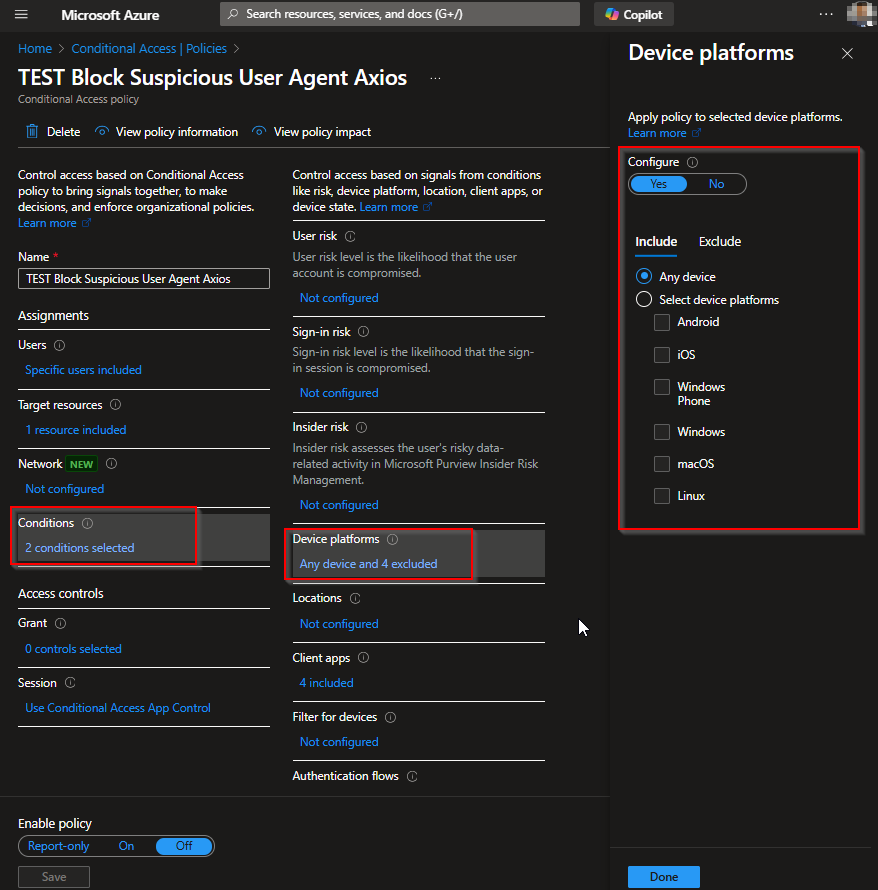
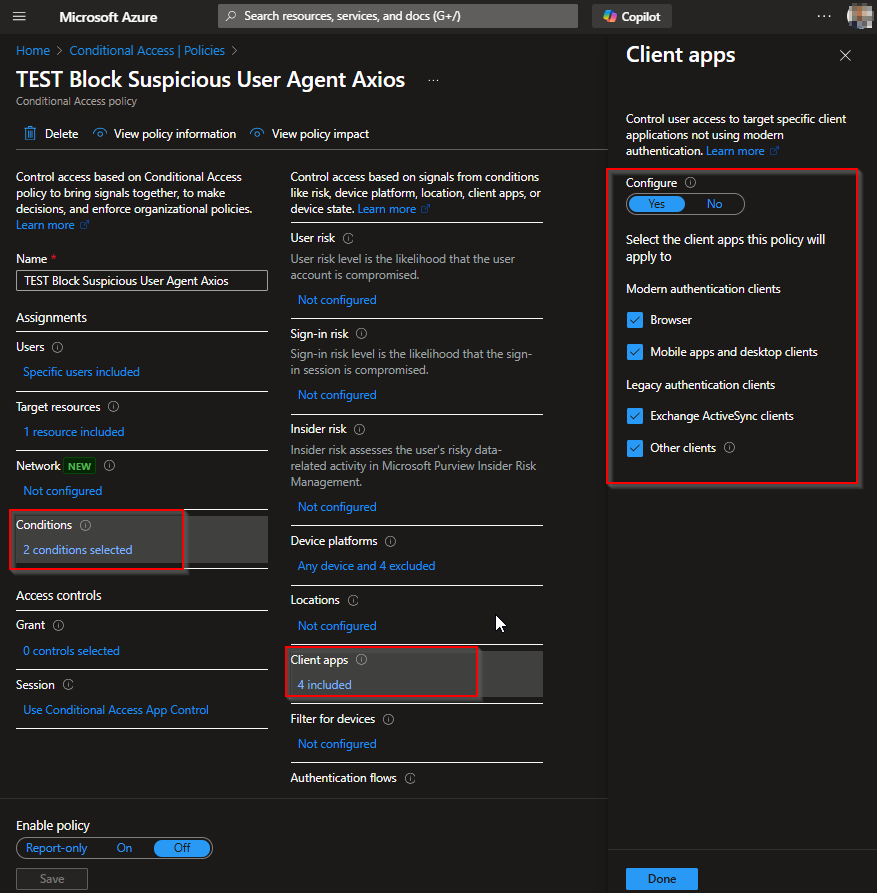
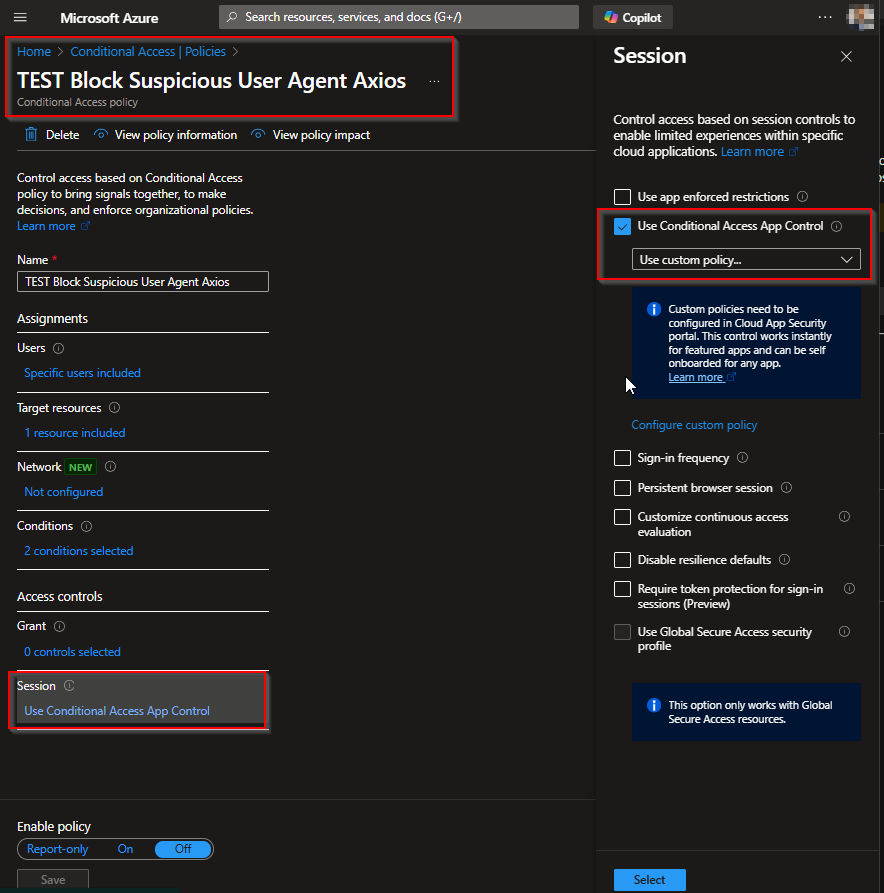
Save and apply the policy.
Trigger MDCA Session Routing (App Detection)
After the CA policy is active, the user must log into the app (e.g., Outlook) to trigger MDCA to detect and begin monitoring the app.
- Open a private/incognito browser window.
- Visit Outlook or Teams.
- Log in with a test account.
- Wait 1–2 minutes.
- Go to: Cloud Apps → Settings → Connected Apps → Conditional Access App Control apps
- Confirm apps like Office 365, Teams, or Exchange appear as Monitored
Note: If not detected, recheck your Conditional Access policy and retry in incognito mode.
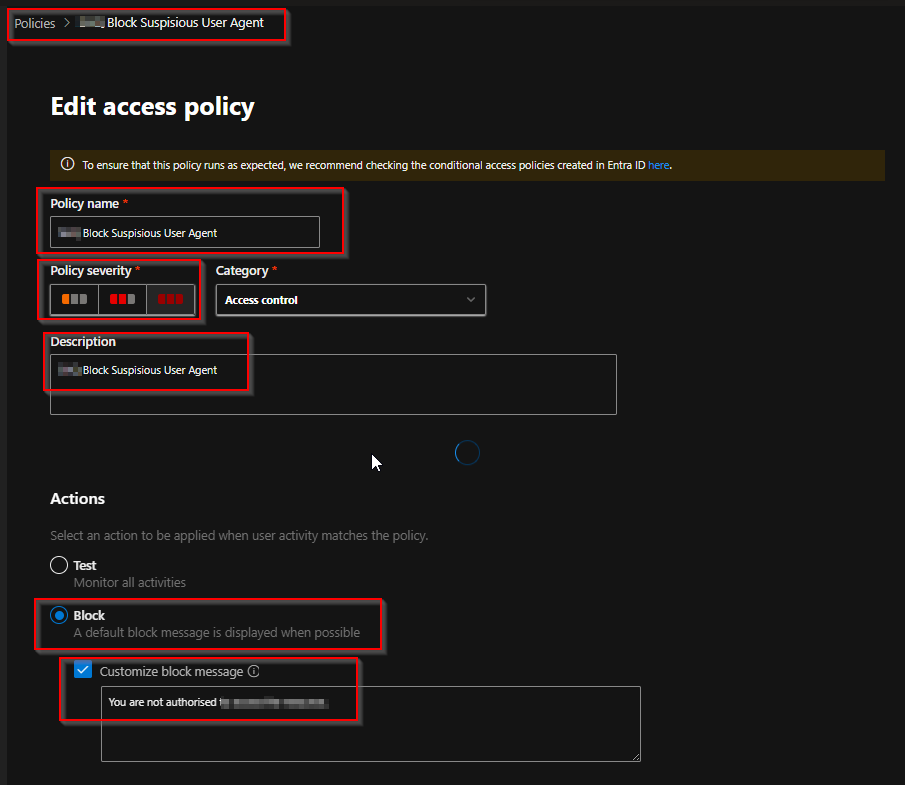
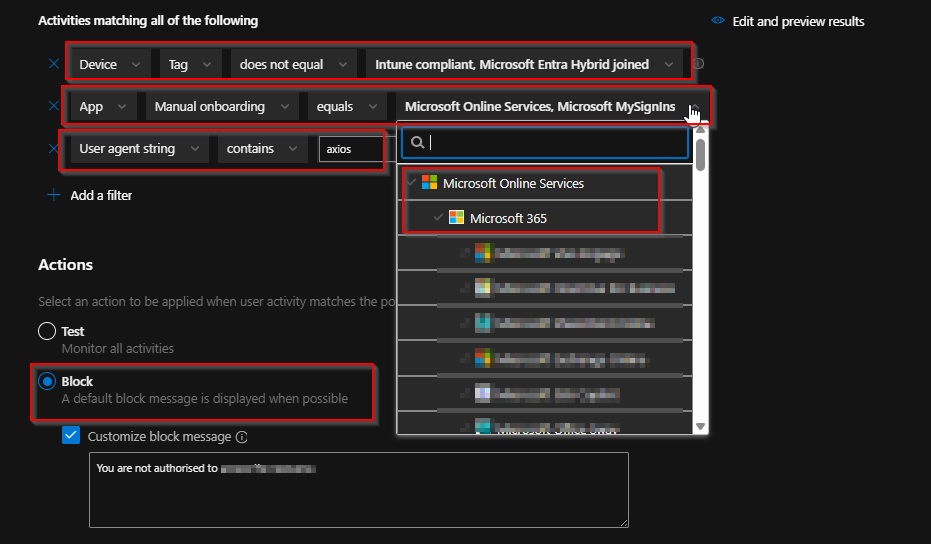
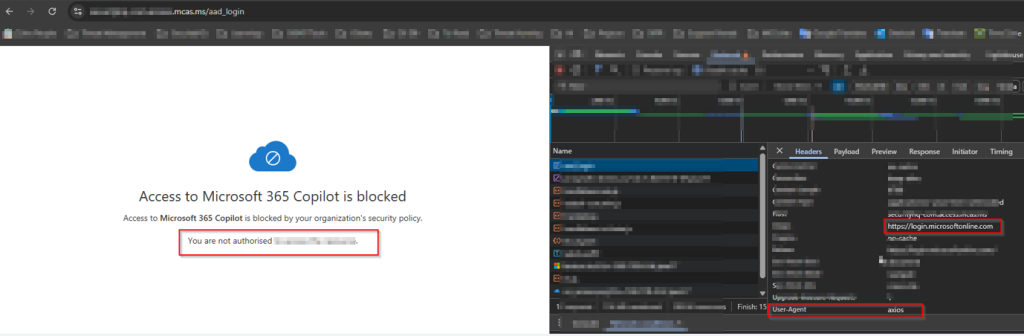
Create MDCA Session Policy to Block Axios
This policy inspects live sessions and blocks any that match certain criteria — in this case, when the User-Agent string contains “axios”.
- In MDCA Portal → Control → Access policies → + Create policy
- Configure the following settings:
Click Create
This will block any Axios-based request to Office 365 apps.


![8 Top Tips to Improve Your Cloud Security [Infographic]](https://sidev.cloud-z.gr/wp-content/uploads/2023/06/Tips-to-improve-Cloud-Security-528x347-1.png)
![10 Tips to Protect Your Data [Infographic]](https://sidev.cloud-z.gr/wp-content/uploads/2021/07/Thumbnail-image-Tips-to-Protect-Your-Data-blog-copy.jpg)






