Key Benefits
62% lower noise-to-signal ratio than other competitors.
Reduce attack surface and maximize the ROI of your existing cyber security technologies.
SHQ Response Platform allows you to visualize, prioritize, escalate and respond to incidents.
450+ security experts, threat hunters, and SANS GIAC certified Incident handlers and forensic analysts.
How It Works
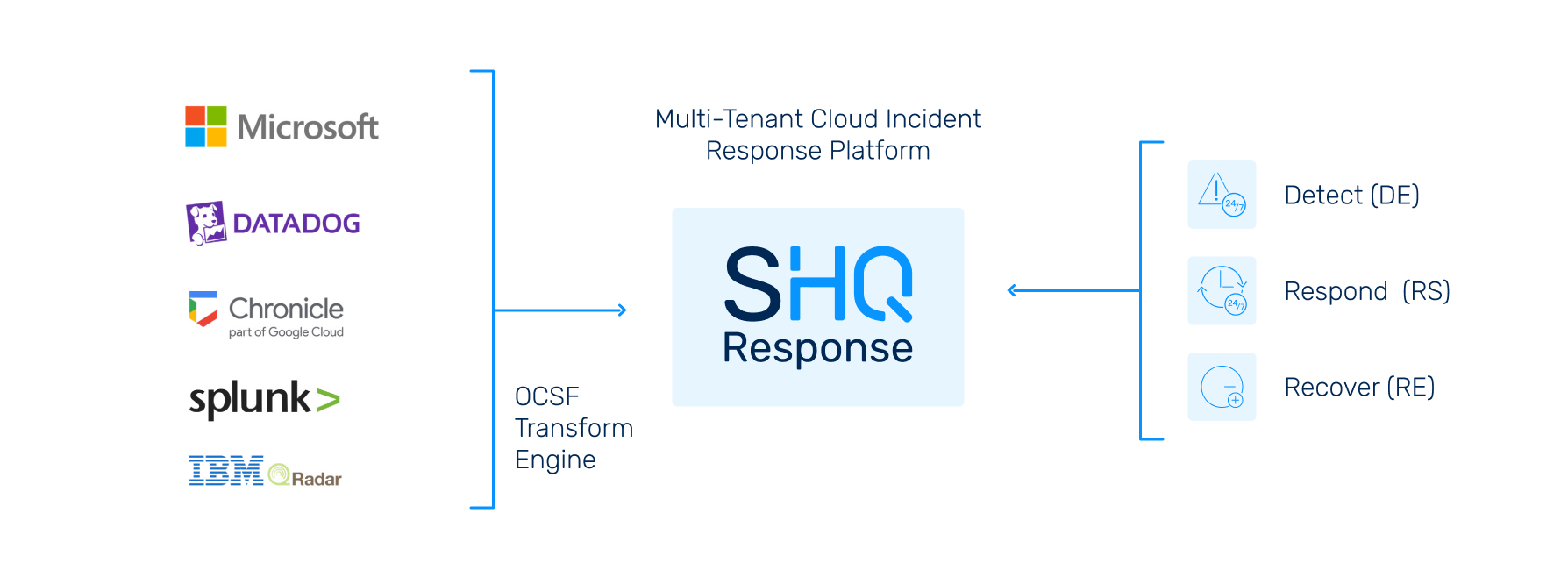
What Does SIEM Detection & Response Do?
Our SIEM Detection & Response alerts you to what is important, provides actions on elements that need investigation, automates activities, and rapidly responds to threats. SIEM also helps organizations stay compliant and up to date with security audits, by enhancing overall security posture.
What the Solution Delivers
Ingestion and orchestration of data from a wide-range of sources including logs, events, and alerts using all major SIEM vendors. Use Our SIEM or Bring Your Own SIEM for us to manage.
SecurityHQ’s Cyber Defense Team triage and investigates threats from correlated alerts, 24/7. Threat detection rules are synchronized to SIEM platforms and resulting detection events are triaged in seconds.
SecurityHQ Incident Response team contains threats to manage the impact of an Incident and provide continuous support for handling threats.
Benefits of SIEM Detection & Response
50% of organizations suffer a breach annually, of which 13% suffer a material loss of $52,500, excluding any loss of revenue or reputation. We mitigate this risk and put in place steps to reduce likelihood of a breach.
The total cost of a breach is $4.88M (IBM), and the annual occurrence rate for material breaches is 6.5% per organization. Safeguard assets, people, processes and data.
The entire infrastructure, including networks, endpoints, and the cloud, is secured. Gain visibility of threats or weak points through a unified data console, and automate incident response to reduce attack impact.
All info-sec frameworks and regulations require logging and auditing, monitoring, and incident response. SecurityHQ automates this reporting to demonstrate compliance.
How SHQ is Different
Agnostic endpoint threat management and reduced exposure.
The market is not limited by the choice of SIEM vendors. Our platform ingests and normalizes data to the common OCSF format. This allows SecurityHQ to plug and play with our customer’s choice of SIEM.









