What Does Phishing Attack Simulation Do?
Phishing Attack Simulation service involves creating realistic, customized phishing campaigns aimed at testing the awareness and response of specific individuals or departments within an organization. The service helps identify vulnerabilities in human behavior, assesses the effectiveness of existing security training, and provides actionable insights to strengthen overall cybersecurity posture.
What the Solution Delivers
Harvesting
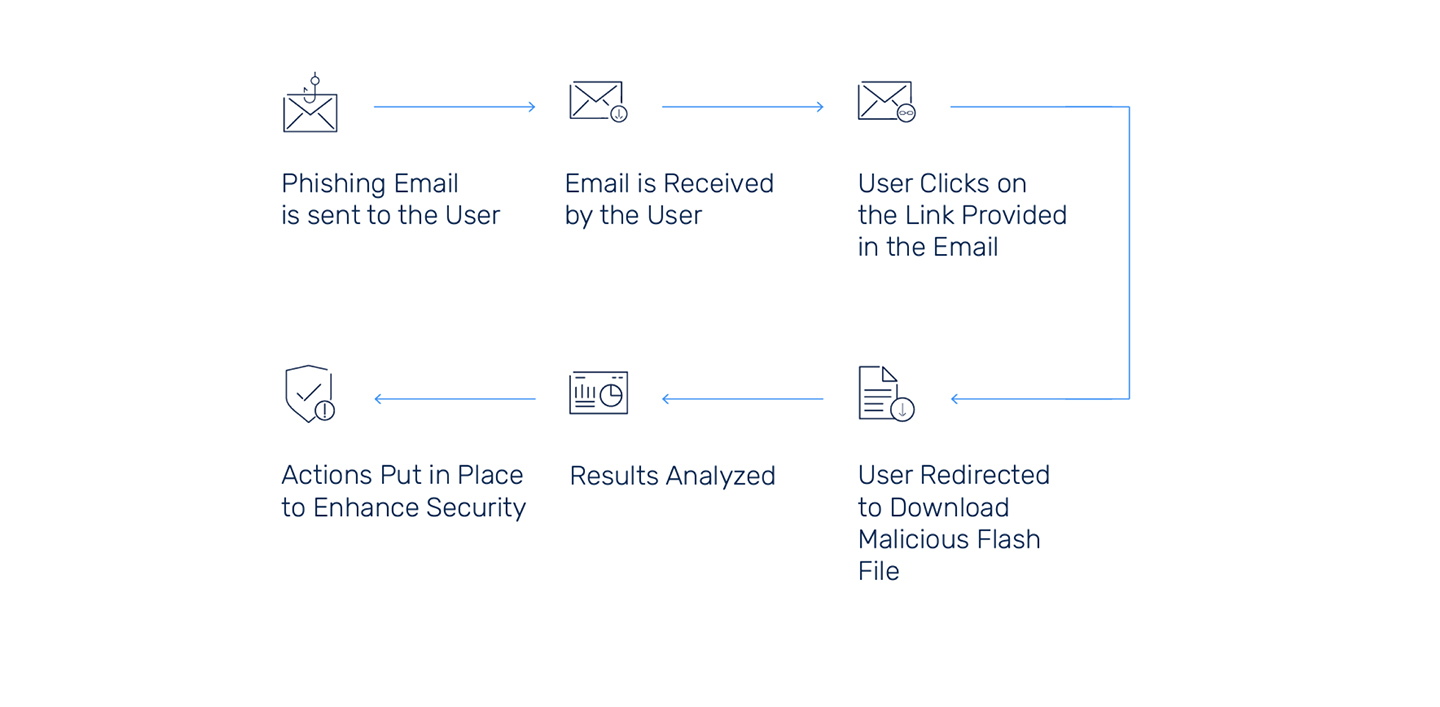
A Phishing campaign is created to impersonate the client’s team with the scenario of creating urgency to immediately start virus scanning via a click to a link given in an email.
Controls
Validate the effectiveness of preventative controls in place, to be able to detect phishing attacks.
Links
Analysts try to trick the user into downloading a malicious attachment. When a user clicks on the link, they are redirected to a phishing domain where a malicious file is executed in the user’s internet browser.
Benefits of Phishing Attack Simulation
Limit the chances of a successful phishing attack.
Instill a culture of awareness from the ground up.
Measure cybersecurity awareness levels and improve them across the business.
Adopt a zero-trust model for enhanced security.
Industry best certifications (OSCP, GPEN, GWAPT, CEH, and more).
Execute phishing scenarios that are most apt for your organization instead of generic attack scenarios.
Organizations that conduct regular phishing simulations experience a 70% reduction in the frequency of these types of security incidents.
How SHQ is Different
Based on the latest attack techniques and compliant with recommended industry-leading practices.
Get a complete view into identifying high-risk users who could be susceptible to phishing attacks.
SHQ Response Platform enhances collaboration in pre-empting, identifying, and mitigating risks before they become security incidents.
Need 24/7/365 Phishing Attack Simulation
for your organization?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.










