Constant Monitoring of Structured and Unstructured Data Traffic.
Overview
Governance with Control Integration with IT management and additional security solutions, so that data protection is comprehensive and clear, throughout the entire organisation.
Effective Compliance with validation activities, via a centralised audit repository, combined with an integrated workflow automation platform.
The Challenge
Few organisations have the in-house skills or budget for monitoring and analysis, audit and compliance, threat prevention, data protection or vulnerability assessment.
The Solution
Managed Data Security covers monitoring and analysis, audit and compliance, threat prevention, data protection, vulnerability assessment and more, all from a dedicated expert.
Key Features
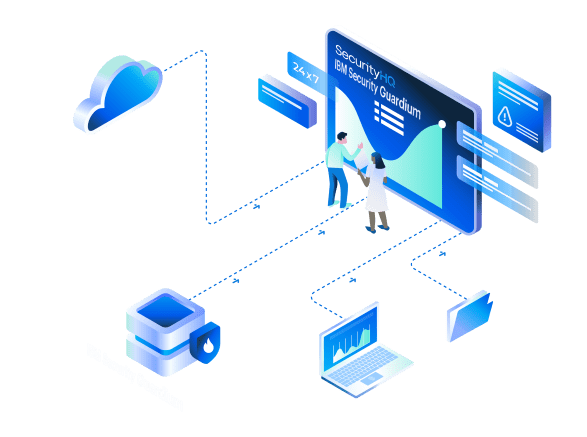
Monitoring and Analytics
- Monitor database in real-time for anomaly detection and policy non-compliance.
- Real time security analytics to detect suspicious transactions or changes.
Audit and Compliance
- Advanced auditing mechanisms beyond native capabilities.
- Centralized auditing and reporting across multiple database environments.
Access Management
- Identify and remove excessive user privileges.
- Manage shared and service accounts, and suspicious user activities.
Vulnerability Assessment
- Complete view into intricate database infrastructures, identifying misconfigurations, and evaluating and mitigating these risks.
Data Discovery & Classification
- A vital stage to identify appropriate policies for various data, dependent on criticality and compliance obligations.
Threat Prevention
- Protection against unpatched vulnerabilities and other database-specific security measures.
Get in Touch!
Talk with one of our experts today.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.