What Does Endpoint Security Do?
Endpoint and end-user devices such as servers, desktops, and laptops on any network can be exposed to exploits, misuse, and malicious actors. Preventative controls are by far the best strategy. But this requires configuration and maintenance by skilled engineers.
Our team provides proactive administration services to deliver complete visibility of all your endpoints. Monitor all communications, from low-level activity to malicious threats, and identify and respond to all elements targeting your endpoints.
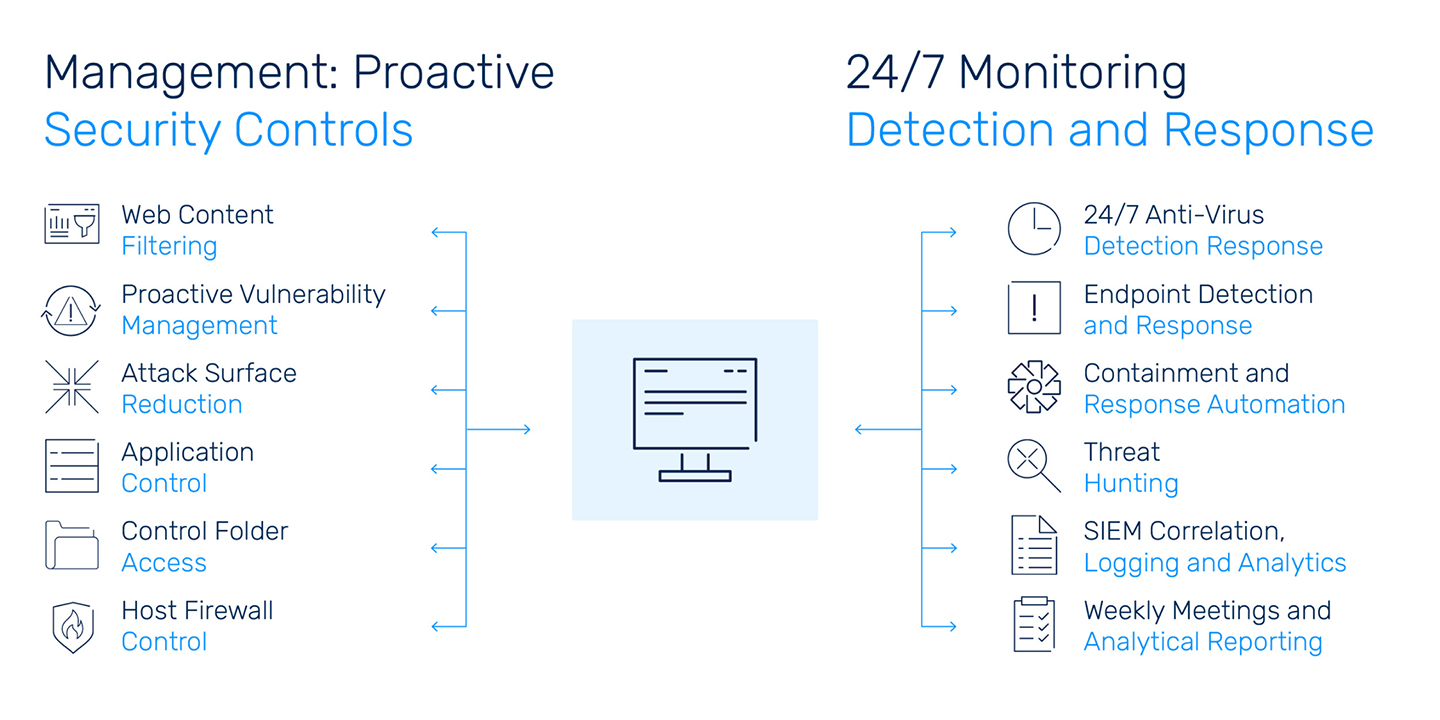
What the Solution Delivers
Remediation
Identify and prioritize endpoint vulnerability remediation processes and remediation requests for approval.
Reduction
Harden and deliver proactive endpoint policy management.
Control
Manage and restrict applications that users can run.
Content Filtering
Manage your corporate web policies to secure your machines against web threats and unregulated content.
Access
Maintain policies for controlled folder access to protect valuable data from malicious apps and threats.
Firewall Control
Configure and maintain host-based, two-way network traffic to block unauthorized network traffic flow and reduce the attack surface.
Benefits of Endpoint Security
Our SOC team responds rapidly to threats by isolating machines or collecting an investigation package.
Our analysts run standard procedures for offline threat hunting, using our query-based threat-hunting tools, and identify risk indicators for further analysis.
We maintain corporate web policies to secure your machines against web threats and help you regulate unwanted content.
Behavioral anomalies are monitored in real-time using queries based on telemetry that collectors process information on using network activities, user login activities, registry and file system changes, and more.
Our SOC team monitors the behavior-based, heuristic, and real-time antivirus protection to alert and respond to malicious activity 24/7.
24/7 transparent and auditable collaboration, Incident Management, Dashboarding, SLA Management, and Customer ITSM integration API.
Companies using endpoint security report 20-30% less downtime after a security incident.
Differentiators
Endpoints and users are the new perimeters. Take control of the risk.
Reduce vulnerabilities, close attack surface, and reduce endpoint risk.
Cyber wars need a cyber army, day and night.
Market-leading endpoint security tools.
Managed Service means no hiring or staffing headaches.
SHQ Response Platform enhances collaboration in pre-empting, identifying, and mitigating risks before they become security incidents.
Need 24/7/365 Endpoint Security
for your organization?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.