What Does Endpoint Detection & Response Do?
Managed Extended Detection & Response for Endpoints involves the continuous monitoring and analysis of your endpoint devices to detect and respond to threats. We help organizations quickly identify security incidents, mitigate risks, and improve their overall endpoint security posture. By partnering with SecurityHQ, we leverage your technologies to ensure a secure environment for your events, protecting participants and sensitive information.
What the Solution Delivers
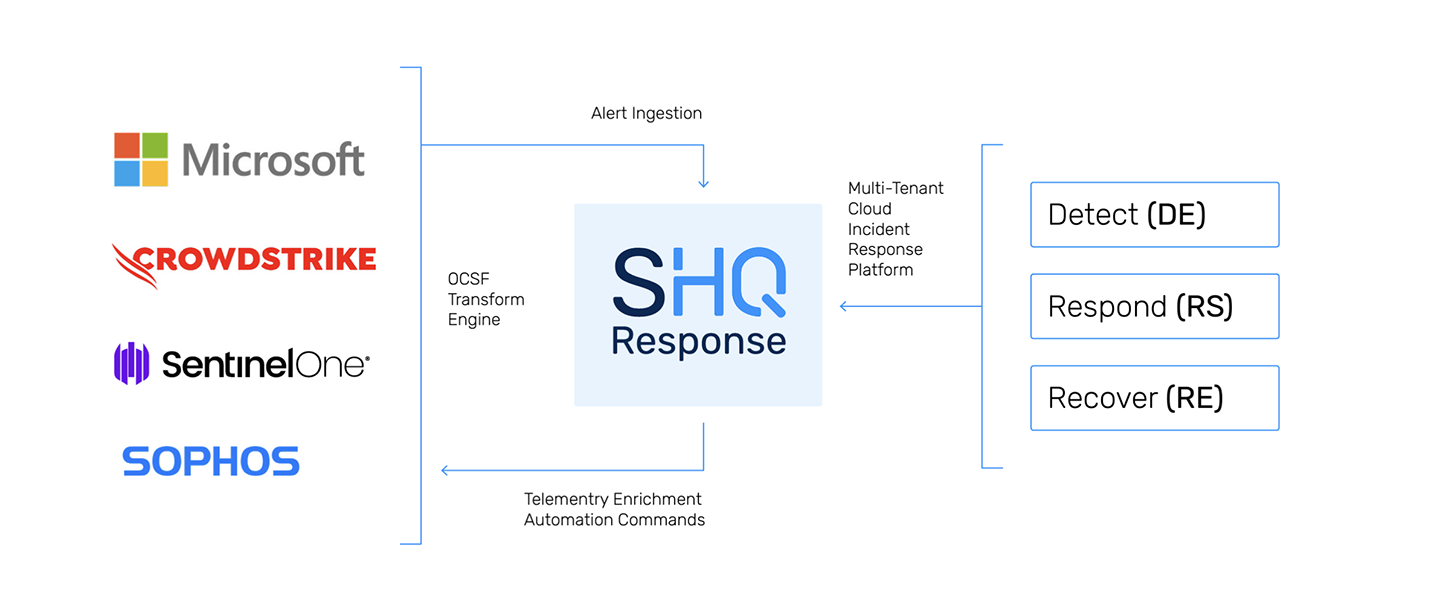
Agnostic
Ingestion and orchestration of data from all leading EDR vendors to deliver an MXDR service. Use Our EDR or Bring Your Own EDR Tool for us to manage.
Detection
SecurityHQ ingests and normalizes alert data and enriches with additional telemetry data to triage Endpoint Threat Events.
Containment
Mitigate the impact of qualified threat events by isolating compromised hosts using preauthorised playbooks.
Eradication
Malicious payloads and artifacts are cleaned and eradicated.
Control
ML profiling is used to deploy Adversary Exposure Mitigation to enforce the least privilege and harden the endpoint against attack.
Benefits of Securing Endpoints
The average response time for cyber insurers is between 24 to 48 hours. SecurityHQ provides breach response forensics within 1 hour.
Adversaries are skilled in evading Endpoint solutions. SecurityHQ monitoring techniques are used to reduce this likelihood with continual analysis of evasion techniques.
We respond to threat detection events in seconds and automate response immediately and continuously 24/7. A swift response is imperative.
Organizations typically utilize only 30% of the features and capabilities of their costly endpoint solutions. SecurityHQ sweats those assets to improve ROI.
Cyber never sleeps. SecurityHQ reduces the customer dependence on hiring, training, and retaining talent that would otherwise attend to endpoint security.
Prioritise threats, formulate action plans, and speed up response time.
60% of breaches involve endpoints being compromised.
How SHQ is Different
60% of Ransomware actors leverage legitimate system tools that evade even the best Endpoint tooling. SecurityHQ profile endpoint services and machine-learned behavior is used to lock down endpoints against attack. Block risky tools and apps, and restrict non-essential firewall communication.
SecurityHQ normalizes data across all endpoints to OCSF to standardize playbooks and allow consistency of quality and the ability to scale the service.
Businesses are often flooded by alerts, and MSSPs can offload responsibility to their customers. SecurityHQ delivers the full response from Detect to Forensics as standard.
SecurityHQ delivers high-fidelity Incidents. The competition churns noisy alerts, whereas SecurityHQ reduces false positives on average 63% less than the competition.
SHQ Response Platform enhances collaboration in pre-empting, identifying, and mitigating risks before they become security incidents.
SecurityHQ drives continuous posture improvement, threat profiling, and baselining using ML-driven data analytics, presented weekly.
Need 24/7/365 Endpoint Detection &
Response for your organization?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

![10 Tips to Protect Your Data [Infographic]](http://sidev.cloud-z.gr/wp-content/uploads/2021/07/Thumbnail-image-Tips-to-Protect-Your-Data-blog-copy.jpg)







