Why SecurityHQ?
62% lower noise-to-signal ratio than other competitors.
Reduce attack surface and maximize the ROI of your existing cyber security technologies.
SHQ Response Platform allows you to visualize, prioritize, escalate and respond to incidents.
450+ security experts, threat hunters, and SANS GIAC certified Incident handlers and forensic analysts.
How It Works
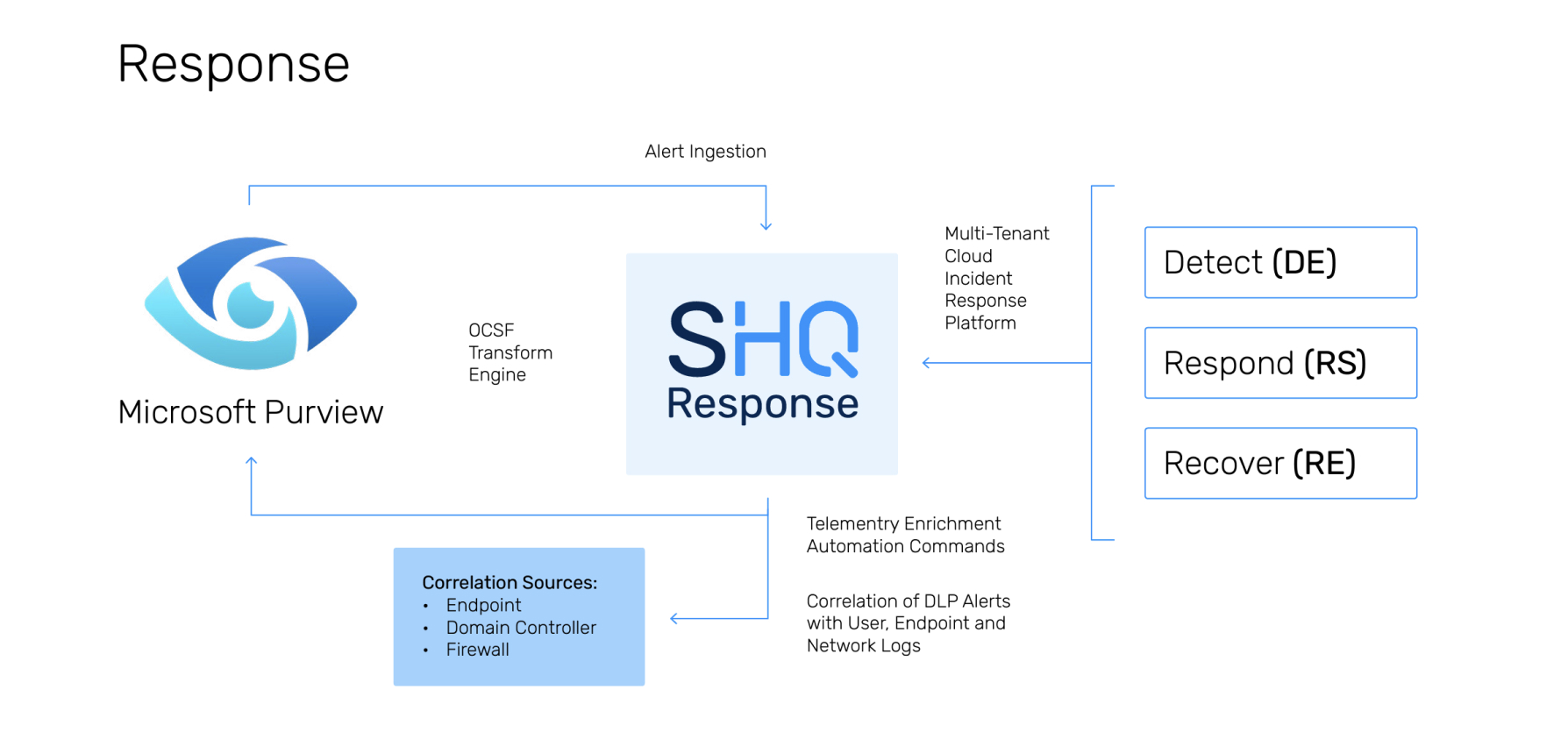
What Does Data Detection & Response Do?
Traditional DLP tools often flood teams with false positives or miss real breaches due to poor configuration and limited context. SecurityHQ’s Data Detection & Response (DDR) service enhances accuracy by combining advanced threat intelligence with expert-led tuning and monitoring to deliver precise detections and accelerate response to real threats.
What We Deliver
Quickly contain threats by quarantining suspicious files, blocking user access, or forcing password resets. These actions help prevent further spread while an incident is being analyzed.
Limit exposure by removing document sharing, applying sensitivity labels, and disabling compromised accounts. Devices can also be isolated from the network to stop ongoing malicious activity.
Real-time monitoring tracks user activity, access patterns, and policy violations. This enables rapid identification and prioritization of threats.
Benefits of Data Detection & Response
Assurance…delivering peace of mind together with reduced costs.
Organizations with well-implemented Data Loss Prevention solutions report a significant reduction in breaches.
The confidence and impact of DDR alerts are corroborated with multi-source correlation across endpoint, firewall, domain controller, and host logs.
SecurityHQ supports compliance reporting against regulations and frameworks such as GDPR, HIPPA, and DORA.
Insider threats are often the hardest to detect. Our data solutions help monitor user behavior and prevent malicious actions before they result in a significant data breach.
How SHQ is Different
Agnostic endpoint threat management and reduced exposure.
SecurityHQ provides Governance consulting on policy, together with Protective Controls management to apply rules and policies. The DDR service integrates across those services to provide end-to-end support.
Data Security Ecosystem
Managed Data Governance
SecurityHQ Managed Risk. Consulting on policy and data categorization. Assists in meeting data protection regulations like GDPR and HIPAA.
Managed Data Protection
implementing rules to restrict data access based on user roles and data sensitivity.
SHQ Response Platform enhances collaboration in pre-empting, identifying, and mitigating risks before they become security incidents.
Managed Data Detect & Respond
Detect and respond to data-related security threats in real-time.