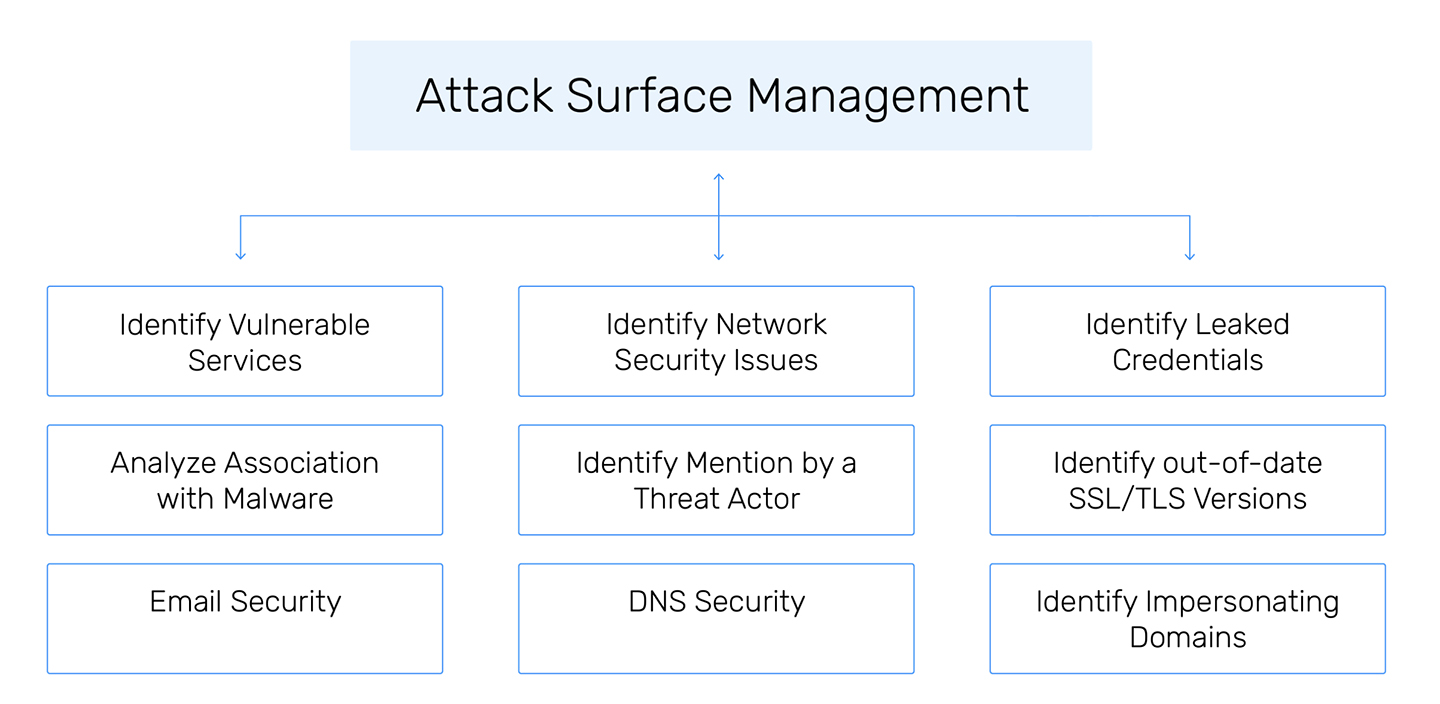
What Does Attack Surface Management as a Service Do?
Attack Surface Management (ASM) involves continuously scanning and analyzing an organization’s digital footprint, including assets, networks, and applications, to identify vulnerabilities and entry points that could be exploited by cyber threats. ASM tools provide real-time visibility into external-facing assets like websites, APIs, and cloud services, allowing organizations to proactively address weaknesses, prioritize risks, and reduce their attack surface.
What the Solution Delivers
Monitoring
Identifies and maps all external-facing assets, including websites, APIs, and cloud services, to ensure no asset is overlooked.
Scans
Scans for vulnerabilities in systems, applications, and configurations that could be exploited by attackers.
Prioritization
Assesses the severity of identified vulnerabilities and helps prioritize remediation efforts based on potential impact.
Monitoring
Provides ongoing monitoring of assets to detect new threats or changes to the attack surface, ensuring proactive defense.
Assists in mitigating and responding to threats by providing detailed insights into exploitable vulnerabilities and attack vectors.
Benefits of Attack Surface Management
ASM provides a comprehensive view of an organization’s entire attack surface, ensuring all external-facing assets are identified and monitored for vulnerabilities.
By continuously identifying and addressing vulnerabilities, ASM helps prevent potential security breaches before attackers can exploit them.
ASM assists organizations in maintaining compliance with security standards and regulations by continuously tracking and securing critical assets and data.
Real-time monitoring and alerts allow for quicker identification of emerging threats, enabling faster response to potential attacks or vulnerabilities.
By preventing breaches and minimizing security risks, ASM reduces the potential costs associated with data breaches, regulatory fines, and reputation damage.
ASM helps organizations minimize unnecessary or exposed assets, thereby shrinking the overall attack surface and making it harder for attackers to find entry points.
Organizations experience a 80% reduction in attack surface exposure.
Differentiators
Real-time monitoring of an organization’s digital footprint, sending immediate alerts for any new or evolving vulnerabilities, misconfigurations, or exposed assets that could be exploited by attackers.
Integrate threat intelligence to assess risks based on actual threat actor tactics, techniques, and procedures (TTPs), allowing organizations to prioritize vulnerabilities that pose the highest risk to their critical assets.
Identify and eliminate unnecessary or exposed assets, reducing the overall attack surface and minimizing the potential entry points for cyber threats before they can be exploited.
The SHQ Response Platform enhances collaboration by pre-empting, identifying, and mitigating risks before they become security incidents.
Need 24/7/365 Attack Surface Management
for your organization?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.










