What Does APT Simulation Do?
Simulate real-world cyberattacks by mimicking the Tactics, Techniques, and Procedures (TTPs) of sophisticated threat actors. This helps organizations identify vulnerabilities in their infrastructure and enhance their overall security posture by proactively addressing potential security gaps.
What the Solution Delivers
Posture Assessment
Identify vulnerabilities, gaps, and weaknesses in your defense mechanisms and evaluate the effectiveness of detection and response systems.
Testing
Enables continuous, automated testing of network defenses without disrupting operations, and integrates with CI/CD pipelines to regularly assess the security of evolving systems.
Threat Scenarios
Simulates advanced cyberattack techniques used by state-sponsored or highly organized criminal groups, and tests resilience against long-term, stealthy attacks.
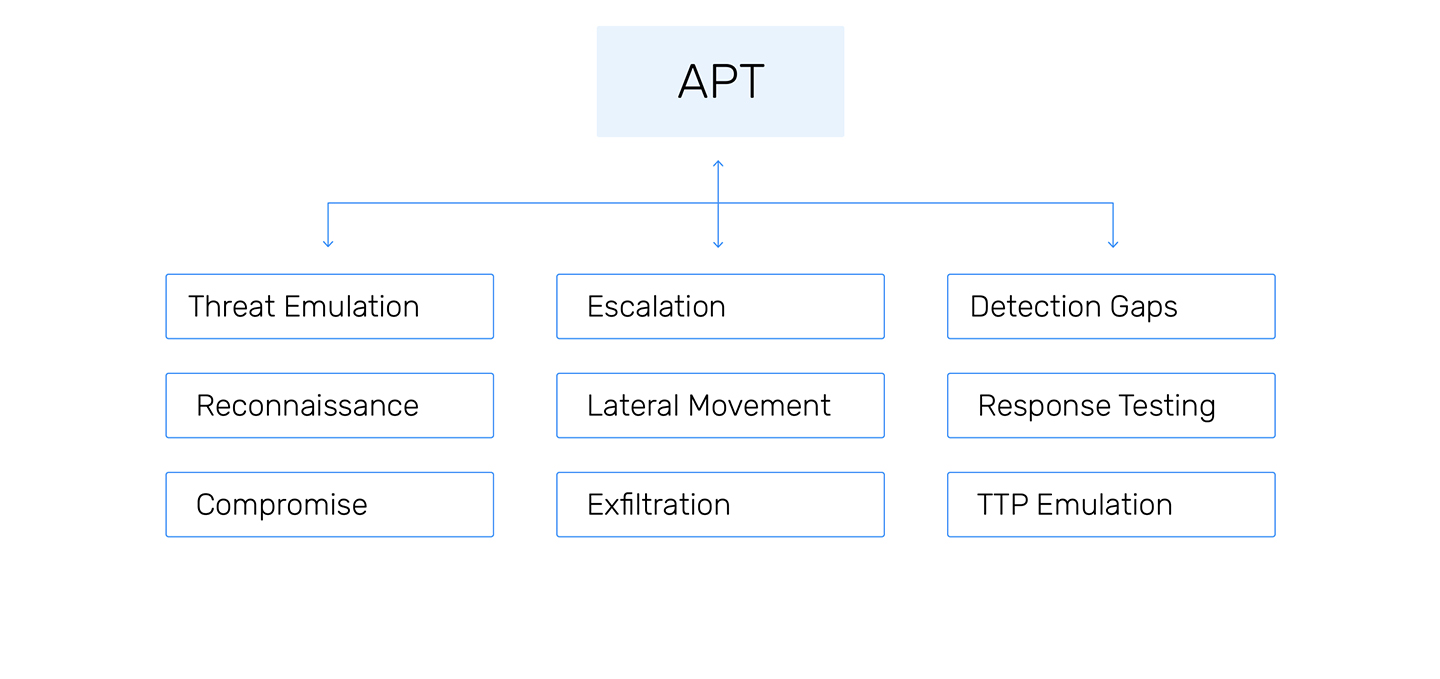
Benefits of APT Simulation
Helps ensure alignment with security best practices and regulatory compliance and demonstrates due diligence in safeguarding sensitive data against advanced threats.
Prepares organizations for advanced threats by simulating actual attacker behavior and improves incident detection, response time, and overall defense mechanisms.
Trains and evaluates the effectiveness of security teams under real-world attack conditions.
Reduces the cost of security audits by automating penetration testing and red teaming exercises and saves potential costs from a breach by fortifying weak points in the infrastructure.
Identify vulnerabilities before real-world attackers exploit them, to reduce the likelihood of a successful attack.
Provides actionable insights and risk assessments based on the results of the simulation. Generates compliance-ready reports for regulatory frameworks like NIST, ISO, and GDPR.
Organizations that conduct regular APT simulations can detect cyberattacks up to 30% faster.
Differentiators
Tailor-made simulations to test specific environments or systems, based on the organization’s unique infrastructure and industry threats.
Real-time monitoring of simulated attack paths, and visual mapping of attacker movements across the network.
SHQ Response Platform enhances collaboration in pre-empting, identifying, and mitigating risks before they become security incidents.
Models a wide range of attack vectors, such as phishing, malware, ransomware, lateral movement, and privilege escalation, and provides end-to-end simulation across the entire cyber kill chain.
Need 24/7/365 Advanced Persistent Threats
Simulation for your organization?
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.