

Incident Management
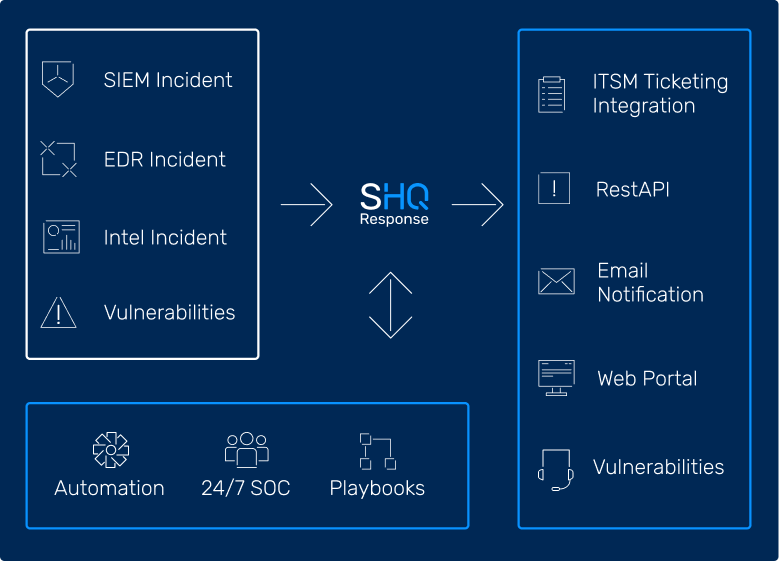
Connect your SIEM for Faster Output and More Oversight
Fully integrated with an enterprise-grade and Gartner leading SIEM technology
The unified interface provides seamless access and collaboration via remote SOC’s, and between tooling (SIEM, EDR, SOAR), IT security teams for the handling of playbooks for incident handling, vulnerability management and change management.
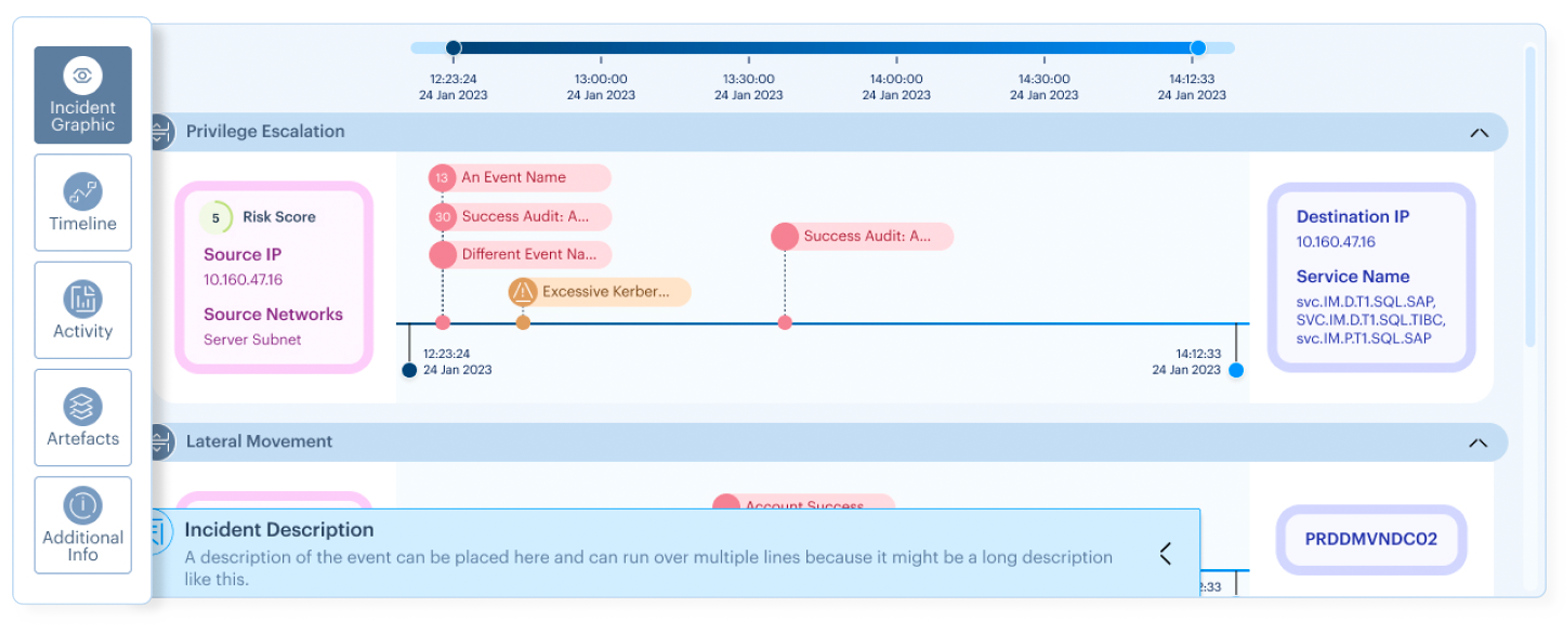
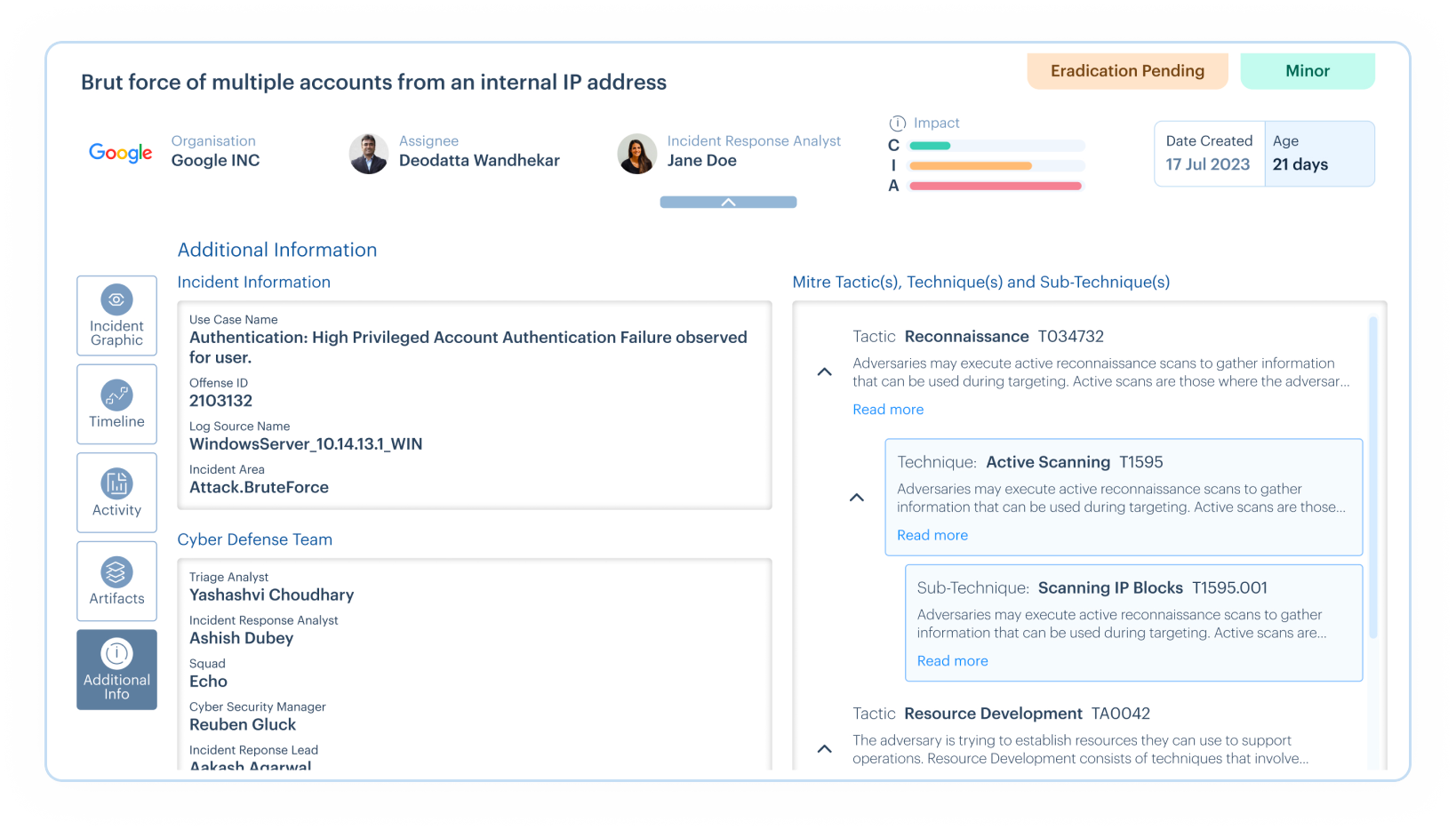
Visualise Incidents and Threats
See all steps of attack and events happened with related actors and victims.
Receive clarity of incident attributes, to illustrate the problems and patterns based on your incident metrics.
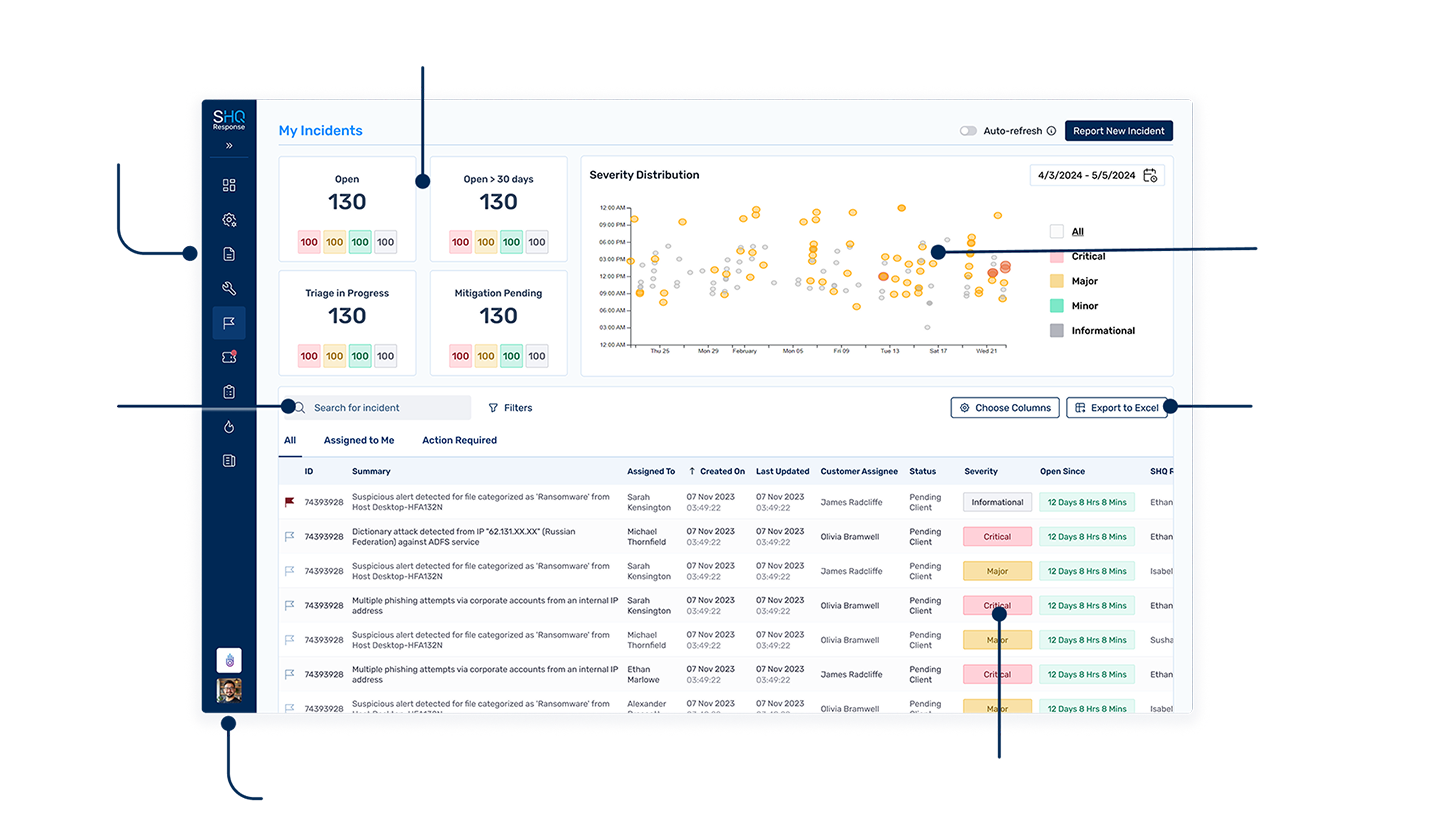
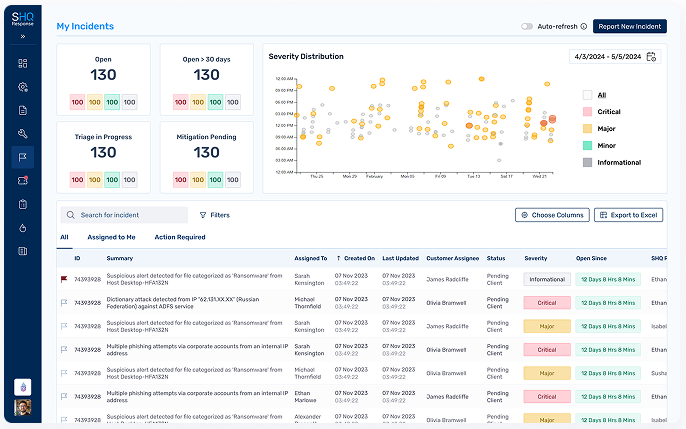
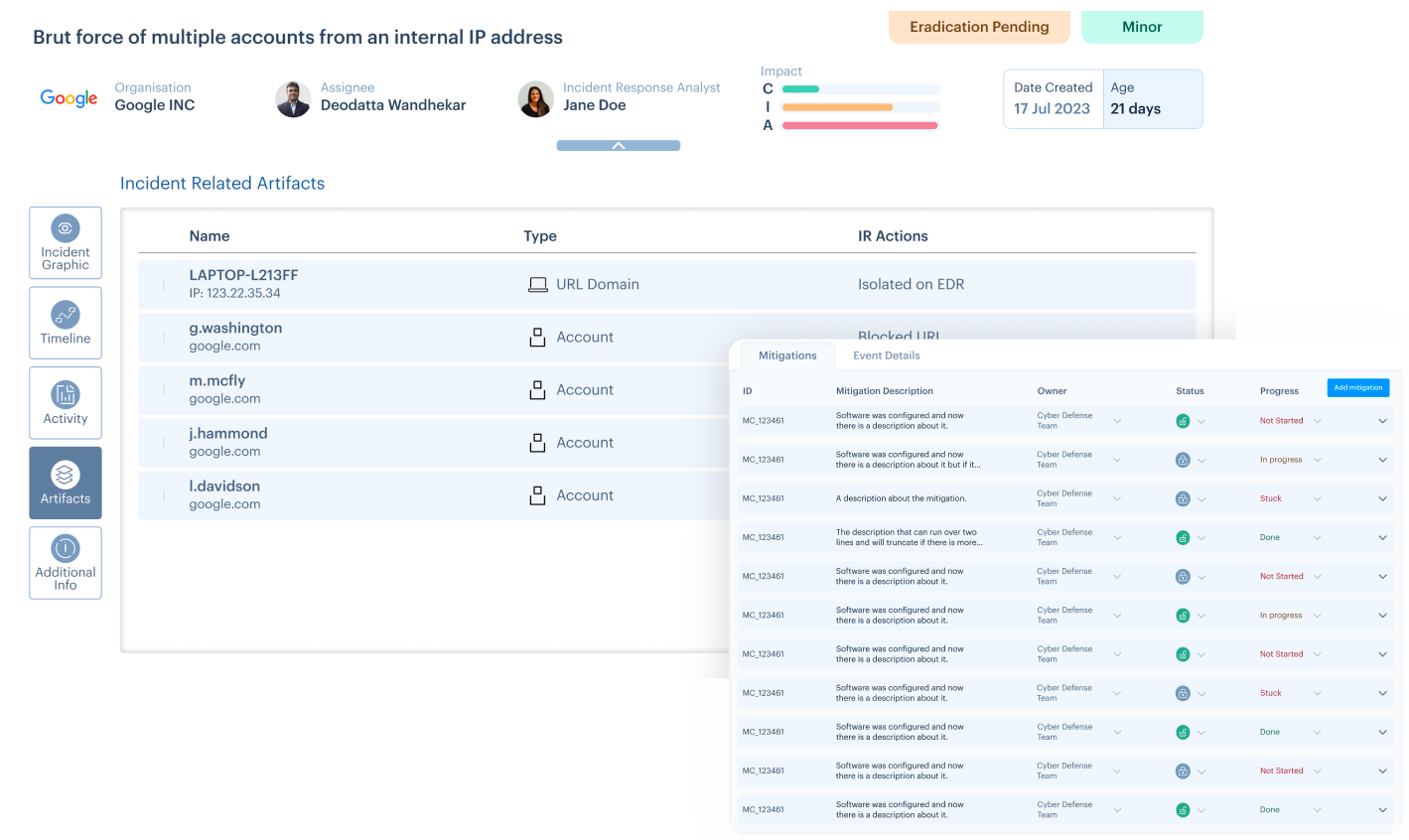
Investigate and Prioritize Incidents
Take Actions that Make a Difference
SHQ Response categorises incidents against MITRE ATT&CK and assigns their risk level, based on the combination of CIA attributes, asset criticality, possible impact and dynamically change it during investigation based on new facts.
Respond and Mitigate to Threats Faster
Accelerate Response via automation.
Incident response requires advanced analysis, combined with an accurate assessment, categorisation, and a playbook for investigation and response. Members can collaborate across IT and Security teams, to prioritise, remediate and rapidly respond to security risks.
Request A Demo Today
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.










