Notes from the Field • 6 MIN READ
What is an Endpoint Detection & Response (EDR) Silencer?
by Eleanor Barlow • Oct 2024
An Endpoint Detection & Response (EDR) silencer is a type of evasion technique or tool specifically created to disable, bypass, or reduce the effectiveness of EDR solutions. Bad actors use EDR silencers to avoid detection, leading to prolonged dwell times (i.e., the amount of time an attacker remains undetected within a network). The longer an attacker goes undetected, the more opportunity they have to exfiltrate data, deploy ransomware, or execute other malicious actions
The EDR Silencer represents a notable tool that is publicly available via open source on GitHub.
Originally developed within Night Hawk, a command-and-control (C2) framework marketed by MDSec Labs, this tool’s capabilities were initially forged.
The fundamental concept of this offensive instrument involves leveraging the Windows Filtering Platform, a built-in suite of system services present in Windows operating systems from Vista 7 onward. The primary purpose here is to obstruct EDR systems from establishing internet communications.
Historically, the Windows Filtering Platform was designed for utilization by security applications such as firewalls, antimalware software, and similar protective solutions.
A Deep Dive on how EDR Silencer Operates
The code harnesses the capabilities of the Windows Filtering Platform (WFP) to dynamically ascertain the processes associated with active EDR solutions, subsequently configuring WFP filters that impede their outbound network traffic across both IPv4 and IPv6 protocols. This sophisticated mechanism effectively disrupts the ability of EDR systems to relay telemetry and alerts to their management consoles, thereby undermining their operational effectiveness.
The command in question simultaneously executes the compilation of the code and initiates the EDRSilencer.exe application, which is engineered to intercept and block any outbound communication directed toward the management console.
x86_64-w64-mingw32-gcc EDRSilencer.c utils.c -o EDRSilencer.exe -lfwpuclnt
EDRSilencer.exe blocked
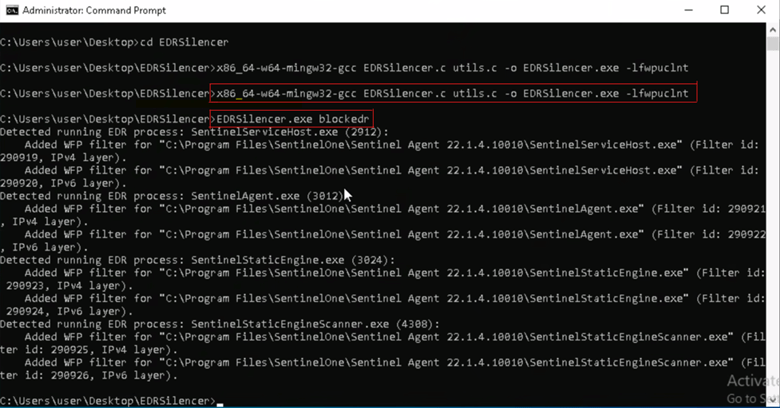
Figure 1: EDR Silencer Initiating EDR Blocking. Source: SecurityHQ Threat Labs
This is a WFP (Windows Filtering Platform) filter that shows a custom outbound filter created by this execution to block outbound traffic. It has been set as a persistent filter.

Figure 2: Windows Filtering Platform Event on the Host. Source: SecurityHQ Threat Labs
Detection
Event Source: Microsoft Windows Security Event Log
Event Category: Process Creation and Success Audit
Event Name: Process creation followed by Success Audit: A Windows Filtering Platform filter has been changed.
Event ID: 5447
Detection and Alerting Parameters: Configurable conditions to tune alert generation include.
Change Information: <Delete/Add>
Filter Information:<Name>
Filter Information:<Persistent>
Layer Information: <Name>
Additional Information: <Filter Action>
These parameters allow for comprehensive monitoring and alerting on activities involving changes to Windows Filtering Platform filters, specifically restricted to known custom outbound filter additions.
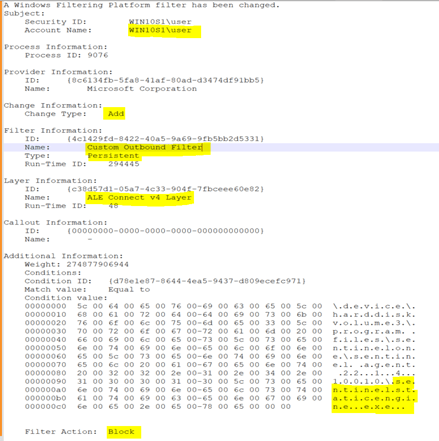
Figure 3: Custom Parameters. Source: SecurityHQ Threat Labs
SecurityHQ Recommendations
Restricting Portable Executables
Prevent executables from running in commonly used directories, like Downloads, Desktop, and Temp. Policies in Group Policy Object (GPO) or AppLocker can block execution from these directories. This approach stops users from inadvertently launching unapproved portable executables directly from common folders.
Group Policy Object (GPO) Restrictions
Configure Group Policies to prevent access to specific command-line interpreters.
- Disable PowerShell: Set policies to restrict powershell.exe and powershell_ise.exe, or configure PowerShell Constrained Language Mode to limit available commands and prevent script execution.
- Block Command Prompt: GPO allows blocking of cmd.exe for non-admin users by navigating to User Configuration > Administrative Templates > System and enabling “Prevent access to the command prompt.
Application Whitelisting and Software Restriction Policies (SRP)
Use tools like Microsoft AppLocker or SRP to restrict access to GCC binaries. Configure rules that allow GCC only on machines designated for development. AppLocker can target applications based on user roles, so non-developer machines won’t have the permissions to execute the compiler.
Principle of Least Privilege
Mandate that all users and applications are endowed solely with the minimal degree of access indispensably necessary for the execution of their designated functions.
For more information about this vulnerability, how it works, and how to protect against it, contact an expert, here.