According to Microsoft, phishing attacks have become the preferred practice of cyber criminals. As attackers are seen using various techniques, tactics, and procedures (TTP’s) to lure targets, common phishing types include impersonating usernames, organizational domains, using cloud storage to host phishing kits and engaging in social engineering attacks with specially crafted attachments that look like attachments commonly used by an organization.
A common phishing practice is to steal account credentials via a phishing email and to use that compromised account to send out phishing emails to contacts listed in that account. Such attacks can leave both the account holder and their contacts vulnerable.
To tackle this threat, many organizations are now deploying email security gateways. This, however, is no longer enough. Even with this in place, user accounts can still become compromised by attackers. These accounts are then used to launch further sophisticated phishing attacks.
Phishing Attack Example
The below phishing attack example begins with a user receiving an email from a compromised third-party sender, with the subject line containing “share a folder”. The email asks for the recipient to open the link in the email body to access the shared folder, which contains a link to the senders SharePoint Online account.
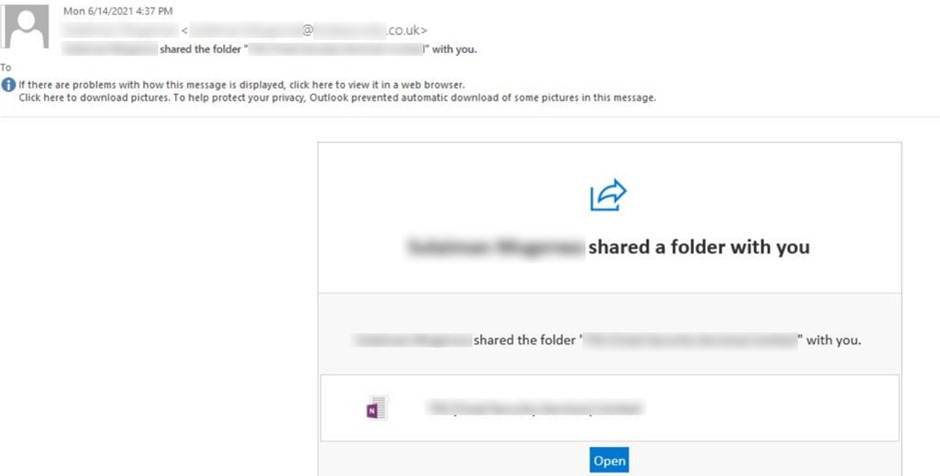
Email format, so the Subject line and Email body, is like the format auto generated by SharePoint whenever any user account is given access to any file or folder on SharePoint. It appears to be a legitimate sender, with no clear indications of the email being a phishing attack. But it is the link in the email that directs the user to OneNote hosted on Senders SharePoint Online. Again, this easily evades controls that are placed to detect risky URLs.
As shown in the below image, once the user clicks on the link, OneNote document is displayed which contains the hyperlink to the phishing page.
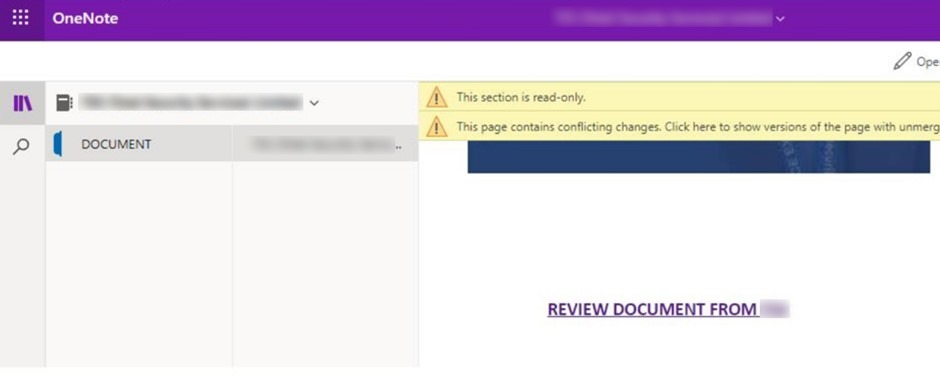
In most cases, a phishing page is hosted on subdomains of “glitch.me”.
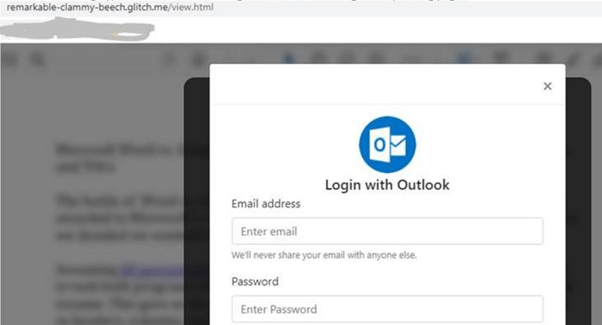
Once the credentials are entered, with the belief that the links are genuine, and login button is clicked, JS script runs and gathers information entered in the form and posts it to another third-party website that the attacker has hold of. The victim is then displayed as a legitimate PDF file on the legitimate website to match the narrative built by the attacker. This is again done to ensure that the attacker is successful in gaining credentials without the user noticing the fraud.
The compromised mailbox is then used to send similar emails providing access to folders to all the email contacts. And the chain goes on.
The reason for sharing the folder and not the file is to bypass various security controls, because the threat is underneath, waiting for user to click. There could be business reasons for sharing a folder, but this needs inspection from your Security team as security controls cannot detect this example of a phishing campaign.
Recommendations
SecurityHQ analysts recommend the following actions:
- Audit and verify all emails from external senders sharing links to access folders.
- If you receive such an email, activate a phishing incident response plan.
- Investigate the mail body and follow the links within.
- Check for any redirectors that take you to third-party sites asking for credentials.
- Do not allow non-standard TLD’s (Top Level Domains).
- Monitor for Secure File/anonymous/company shareable link creation in Online SharePoint.
- Closely monitor mailbox logins for the users who clicked on the phishing link.
SecurityHQ Analysts have seen 100% true positive cases, especially when shared folder name matches with sender’s domain or company name.
For more information on how to secure your systems, people, and processes, speak with a SecurityHQ expert. Or, if you suspect an incident, report it here.










