Notes from the Field • 10 MIN READ
New Wave of Spear Phishing Emails within HTML Attachment- An Analysts View
by Ninad Chogale, Eleanor Barlow • Jul 2023
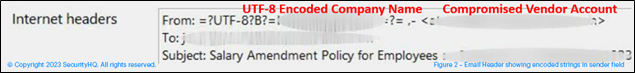
SecurityHQ have recently observed a new wave of Spear Phishing attacks. In this wave, the threat actor uses a html file to compromise vendor accounts. Figure 1 below shows an example in which an email was received from a compromised vendor account, displaying the company name of the compromised account itself.

How are Phishing Attacks Successful?
Attackers victimize users by adding sense of urgency to their language that drives curiosity, and makes the user want to open the html attachment.
In one of scenario, we have observed the attacker use a UTF8 encoded string to show the display name as target account’s company name.
What This Means from an Analysts Point of View
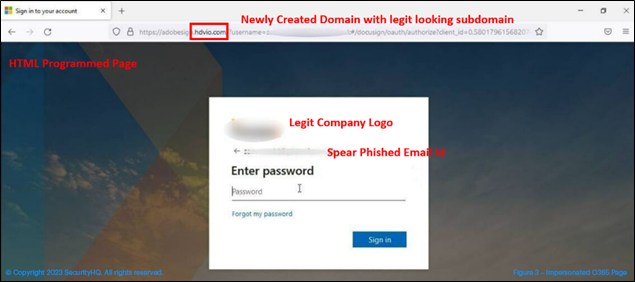
The html attachment, when selected, redirects to a legitimate looking subdomain, hosted on a newly created site. This site impersonates the Microsoft O365 page.
The Microsoft page is specifically designed as per the recipient’s company page and will be designed with the specific user in mind. Once you enter the credentials, it will show an error message, like server error, wrong password, or server timed out, which will ask you to re-enter the credentials. When you re-enter the credentials, it will redirect you to legitimate SharePoint sync issue page, and your existing session will be lost.
While this is happening on the front end, in the back end your credentials are getting shared in plain text. Figure 4 shows this scenario, where credentials, along with user agent and location information, has been sent to a telegram chat. It is this information that is used by the attacker to login to the compromised account.
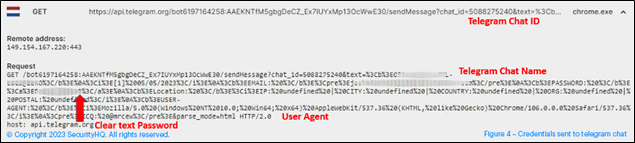
Figure 4 – Credentials sent to telegram chat.
SecurityHQ’s Recommendations
Recommendations to the Analyst:
- Block any non-standard attachment for email communication.
- Add a precautionary message in email body or subject line like “be cautious about this email”.
- Block connections to newly created sites on Proxy.
- Enable MFA for email login.
- Implement a vendor security plan.
Recommendations to the User:
- Never open emails from an unknown sender.
- Check for typos- this is often a giveaway of a bad email.
- Don’t share your sensitive information via emails.
- Hover over links, but don’t click on them.
- Attachments can be dangerous, only open them if you are sure they are from a trusted source.
- If it sounds too good to be true, it probably is.
- Keep devices up to date.
- Regularly check your accounts, and update password policies.
Next Steps!
Since attackers are creating new techniques to evade detection on a regular basis, we can’t just protect users by blocking IOC. To enhance security measures, you need a 24X7 SOC setup with advanced, threat intel based and behavioral use cases. SecurityHQ guides organisations with proper plans in terms of Architecture gaps, Vendor account Policies and much more.
To speak with an expert, contact the SecurityHQ team here.












