Insider threats account for over 30% of account compromises
Overview
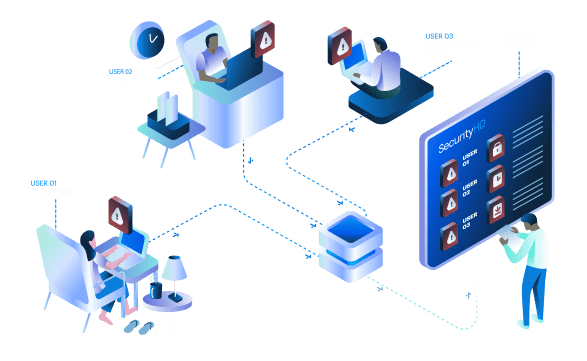
By using ML algorithms, we categorise patterns of user behaviour, to understand what constitutes normal behaviour, and to detect abnormal activity. If an unusual action is made on a device on a given network, such as an employee login late at night, inconsistent remote access, or an unusually high number of downloads, the action and user is given a risk score based on their activity, patterns and time.
The Challenge
Many threats and risks cannot be detected by SIEM, IPS, and other security tools.
The Solution
SecurityHQ’s SOC teams deliver real-time advanced anomaly detection, to identify malicious and anomalous activity arising from zero-day exploits, as well as malware and insider activity.
Key Features
Real-Time Threat Detection
- Real-Time Detection of Every Phase of an Attack
- Leverage Anomaly Detection Platform
Variety of Detection Triage
- Track Misconfigurations
- Track High-Risk Applications that can Enable or Obscure a Cyber-Attack
Smart Automation & Rapid Response
- Central Support for Automation
- Increased Accuracy
- Shortened Recovery Time for Remediation
Data Science Detection
- Combined Data Science, ML & Behavioural Analysis
- Reveal Characteristics of Malicious Activity
- No Need for Signatures
Active Attack Detection
- Correlate a Threat Certainty Index
- Automatically Consolidate all Detections and Confidence Scores
- Reveal Specific Hosts that Pose the Greatest Risk
Prioritising Key Assets
- Receive a Visual Map of Threats, Hosts and Key Assets
- Ensure an Overall Context of Threats
Get in Touch. Talk with one of our experts today.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.